Acerca de nosotros
¿Qué es Recarga Digitel®?
Es una red de distribución de recargas en Argentina y de otros países, que ofrece el servicio de recarga de celulares, pines de tarjetas telefónicas (móviles y fijos) y otros productos prepagos.
La plataforma de negocios permite realizar:
- Recarga de saldo a celulares
- PIN de tarjetas telefónicas
- Recargas de TV
- Cobros o pagos de servicios
- Pagos de transporte
- Enviar o recibir dinero
- Tarjetas de regalo
Recarga Internacional
Recarga tu celular, el tu familia y el de tus amigos, disponible para todas las compañías que operan en más que 140 países.
Carga crédito y envía saldo desde cualquier parte a cualquier persona en cualquier momento.
No requiere tener tarjeta de débito o crédito, ni cuenta bancaria.
Buscamos agentes en todo el país
Gift Cards
Compre de forma segura tarjetas de regalo con descuento
 Las tarjetas de regalo más requeridas aparecen a la venta todos los días, y puedes encontrar buenas ofertas en Nubepin
Las tarjetas de regalo más requeridas aparecen a la venta todos los días, y puedes encontrar buenas ofertas en Nubepin
Simplemente busque o explore tarjetas de regalo utilizando nuestro sitio web. Nuestro mercado tiene una amplia selección de marcas y modelos. Podrás comprar con entrega automática para una experiencia de compra más rápida y fluida. ¿Tiene preguntas? Simplemente solicite información adicional que pueda ayudarlo a realizar una compra más informada.
¡Sumamos AstroPay Card!
 AstroPay Card es una tarjeta virtual prepaga que es aceptada en cientos de sitios online de todo el mundo. Podes llevar a cabo depósitos en páginas web asociadas con AstroPay sin revelar tu información bancaria. Es elegida por los usuarios por ser instantánea, flexible en sus límites, confidencial y segura.
AstroPay Card es una tarjeta virtual prepaga que es aceptada en cientos de sitios online de todo el mundo. Podes llevar a cabo depósitos en páginas web asociadas con AstroPay sin revelar tu información bancaria. Es elegida por los usuarios por ser instantánea, flexible en sus límites, confidencial y segura.
- Preguntas frecuentes
- ¿Cómo tener carga virtual para mi negocio?
- ¿Cómo funciona el sistema?
- ¿Cuáles son los requisitos?
- ¿Cómo comprar el saldo?
¿Cuál es el beneficio?
- Disponibilidad de saldo las 24 horas
- Cuenta bancaria con tu número CVU
- Cobro con tarjeta de débito
- Comisiones
- Auto comisión adicional por prestación del servicio 20% o más sobre valor de cada recarga a criterio de cada comercio – No viola la Ley 24.240

¿Cómo tener saldo virtual?
 Presentamos un nuevo servicio de recarga de saldo para celulares, pines de tarjetas telefónicas y otros productos prepagos. Plataforma disponible para todos los modelos de terminales digitales existentes en el mercado.
Presentamos un nuevo servicio de recarga de saldo para celulares, pines de tarjetas telefónicas y otros productos prepagos. Plataforma disponible para todos los modelos de terminales digitales existentes en el mercado.
¿Guia paso a pasa para tener carga virtual?
Desde cualquier tipo de terminal: celular o tablet y/o desde una PC laptop o computadora.
¿Cómo funciona el sistema?
El método de operaciones de Recarga Digitel® es simple y disponemos de varias opciones para realizar las transacciones.
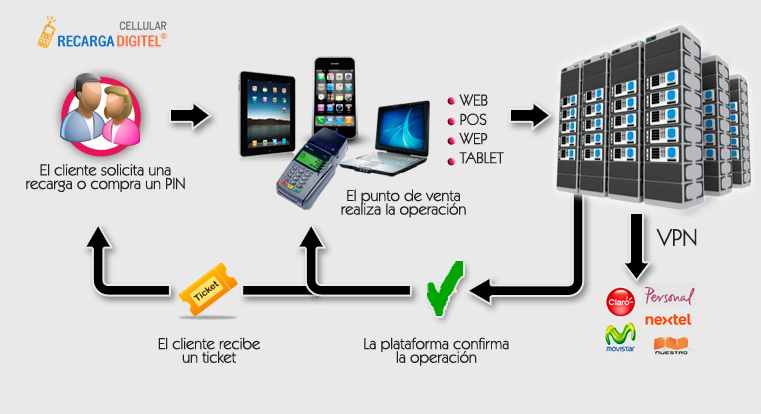
¿Cuáles son los requisitos?

- Enviar tus datos
- Comprar el saldo prepago
¿Cómo comprar el saldo?
- Punto efectivo Pago Fácil o Rapipago
- Depósito o transferencia bancaria

























